2025 Top strategic Technology Trends
Gartner’s 2025 Strategic Technology Trends for Preparation
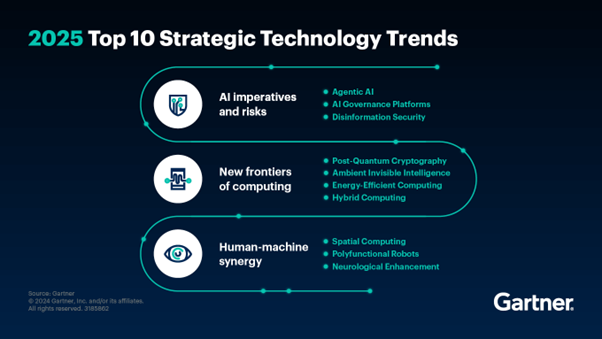
AI imperatives and risks
New frontiers of computing
Human-machine synergy
AI imperatives and risks
1. Agentic AI
Agentic AI refers to software programs that are designed to independently make decisions and take actions to achieve specific goals. These programs combine various AI techniques with features like memory, planning, sensing the environment, using tools and following safety guidelines to carry out tasks to reach objectives on their own.
Use cases
• Empowering workers to develop and manage more complicated, technical projects — whether microautomations or larger projects — through natural language
• Automating customer experiences by using data analysis to make highly calculated decisions at each step
• Changing decision making and improving situational awareness in organizations through quicker data analysis and prediction intelligence
2. AI governance platforms
AI governance platforms help manage and control AI systems by ensuring they are used responsibly and ethically. They allow IT leaders to make sure AI is reliable, transparent, fair and accountable while also meeting safety and ethical standards. This ensures that AI aligns with the organization’s values and broader societal expectations
Use cases
• Assessing potential risks and harms that AI systems may pose, such as bias, privacy violations and negative societal impacts
• Guiding AI models through the model governance process to ensure all appropriate gates and controls are followed during the model life cycle
• Tracking usage, monitoring AI system performance, auditing decision-making processes and ensuring AI systems remain aligned with governance standards over time
3. Disinformation Security
Disinformation security is designed to help identify what can be trusted. The goal is to create systems that ensure information is accurate, verify authenticity, prevent impersonation and monitor the spread of harmful content.
Use cases
• Detecting use of synthetic media in authorized contexts (identifying verification, real-time communications or claims validation)
• Intelligence monitoring for narratives spread through mass or social media, such as those targeting an executive leadership team, products, services or brand
• Preventing the impersonation of individuals doing business with an organization, such as employees, contractors, suppliers and customers
New frontiers of computing
4. Post-Quantum Cryptography
Post-quantum cryptography (PQC) refers to cryptographic methods designed to be secure against the potential threats posed by quantum computers
Use cases
• Future-proofing your systems to ensure that sensitive financial data remains secure even in a quantum computing world
• Safeguarding valuable intellectual property from cyberthreats, including future quantum attacks, ensuring competitors or hackers cannot decrypt confidential information
• Ensuring encrypted messages, contracts and operational data cannot be intercepted or decrypted by quantum- powered adversaries
5. Ambient Invisible Intelligence
Ambient invisible intelligence refers to the widespread use of small, low-cost tags and sensors to track the location and status of various objects and environments. This information is sent to the cloud for analysis and record keeping. These technologies will be built into everyday objects, often without the user noticing them.
Use cases
• In a retail environment, automatically adjusting lighting, music and product recommendations based on customer behavior
• Monitoring how employees use office spaces and adjusting environmental factors automatically
• In healthcare, continuously monitoring patients without requiring wearable devices, enabling real-time responses to emergencies
6. Energy- Efficient Computing
Energy-efficient computing refers to designing and operating computers, data centers and other digital systems in ways that minimize energy consumption and carbon footprint.
Use cases
• Cutting data center costs by reducing the power consumption of servers and cooling systems
• Sustainable product development: using energy-efficient computing to design products that consume less energy
• Using smart power management systems, reducing power consumption across office networks
7. Hybrid Computing
Hybrid computing combines various technologies – such as CPUs, GPUs, edge devices, ASICs, and neuromorphic, quantum and photonic systems – to solve complex computational problems.
Lt creates a hybrid environment that uses the strengths of each technology.
Use cases
• Cost-efficient scalability: keeping critical workloads in-house for security reasons, while using the cloud to handle peak loads during busy seasons
• Enhancing data security and compliance: storing sensitive data on-premises, meeting strict data privacy regulations, while using the cloud for less sensitive operations or analytics
• Accelerating innovation and development: leveraging cloud-based development tools, while maintaining secure, on- premises environments for production
Human-machine synergy
8. Spatial Computing
Spatial computing augments the physical world by “anchoring” digital content in the real world, enabling users to interact with it in an immersive, realistic and intuitive experience.
Use cases
• Collaborating with your team in immersive 3D environments, making remote meetings more interactive and effective
• Creating lifelike simulations for employee trainings to emulate hands-on learning, reducing training costs and risks while improving skill acquisition and retention
• Navigating stores/purchasing decisions with an interactive virtual assistant to improve the shopping experience, driving higher engagement and sales
9. Polyfunctional Robots
Polyfunctional robots are machines that can perform multiple tasks, following human instruction or example. They are flexible in both design and how they operate.
Use cases
• In a warehouse environment, handling multiple tasks such as picking, packing and transporting goods
• Assisting in healthcare, performing various tasks such as delivering medical supplies, assisting patient mobility or even disinfecting spaces
• In field servicing, inspecting equipment, performing routine maintenance and repairing breakdowns in remote or hazardous environments
10. Neurological Enhancement
Neurological enhancement is the process of improving a human’s cognitive abilities using technologies that read and decode brain activity and optionally write to the brain.
Use cases
• Reducing trainee surgeons’ residency duration by a full year
• Personalizing educational material for students in real time
• Reducing workplace accidents and injuries, and industrial disasters
• Improving recruitment and retention by identifying compatible colleagues via neurodata
If you want to stay updated on the latest IT technologies and industry trends selected by Cloocus, subscribe to the "Cloonews" and conveniently receive various insights!
Related Posts

Cloocus Corp.
[United States] 500 7th Ave. Fl 8 New York, NY 10018 | Tel.+1 408.7722024 | E-mail.info_us@cloocus.com
[Malaysia] A-3A, Block A, Level 3A, Sunway PJ51A, Jalan SS9A/19, Seri Setia, 47300 Petaling Jaya. | Tel.+6016 331 5396 | E-mail.infoMY@cloocus.com
[Korea Headquarter] 6, Nonhyeon-ro 75-gil, Gangnam-gu, Seoul, Republic of Korea 06247 | Tel.02-597-3400 | E-mail.marketing@cloocus.com
[Korea Busan Campus] 55, Centum jungang-ro, Haeundae-gu, Busan, Republic of Korea | Tel.051-900-3400
[Japan] ARK Hills Front Tower, 2-23-1 Akasaka, Minato-ku, Tokyo | Tel.+81 3.5575.7808 | E-mail.infoJP@cloocus.com
Copyrights 2024 Cloocus co.,ltd. all rights reserved.




