Cloud-Based Vulnerability Attacks Increase by Over 95% Compared to Last Year
Since the activation of remote work due to COVID-19, the importance of cybersecurity has grown immensely amid a series of large-scale hacking incidents. With fractures in the international order following the wars in Russia and Ukraine, various countries like China and Iran are engaged in global espionage through destructive ransomware. As a result, the current U.S. administration under Joe Biden and big tech companies are emphasizing cybersecurity, leading many companies to join the competition in the cybersecurity industry.
CrowdStrike, the top U.S. cybersecurity company, revealed in their “2023 CrowdStrike Global Threat Report” that cyberattacks have increased by 95% compared to the previous year. As the transition to cloud environments accelerates, cloud vulnerability attacks are also on the rise. Notably, CrowdStrike Intelligence tracked over 200 attackers, including 33 new ones. The addition of these 33 attackers represents the highest number of new attackers identified in a year.
Among these attackers, more than 20 are classified as profit-driven “Spiders.” They played significant roles in large-scale attacks targeting recent communication, BPO, and technology companies, including the “Scattered Spider” and “Slippery Spider.” The Log4Shell vulnerability, which emerged at the end of 2021, remains resilient. In 2022, cybercriminals extensively exploited the 900 vulnerabilities and 30 zero-day vulnerabilities that Microsoft announced patches for. Alongside known vulnerabilities like ProxyNotShell and Follina, newly discovered vulnerabilities were widely exploited by state-sponsored and cybercriminal attackers to bypass patches.
Based on the increased activity of China-Nexus spies across 39 global industry sectors and 20 regions, all companies should be vigilant against China-related threats. There was a significant increase in cases of Russian-Nexus attackers using information collection tactics and fake ransomware. The report also discusses the behavior, trends, and tactics of politically motivated hackers known as “Hacktivists” aiming to threaten international order through cybercrimes, reflecting the growing security threats in the cloud environment as a global cyberwarfare.
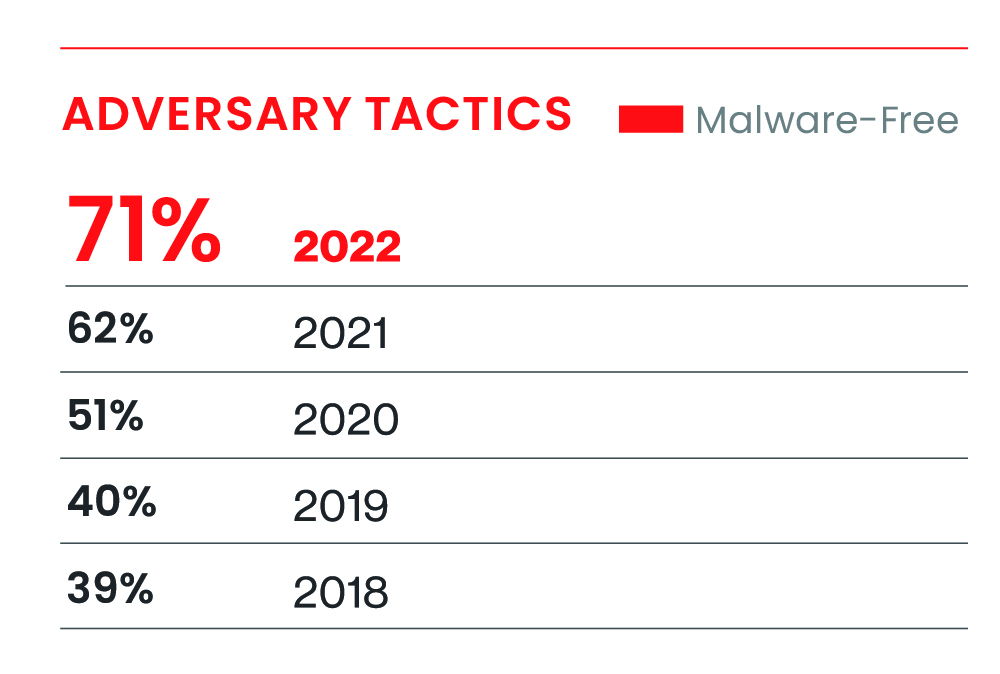
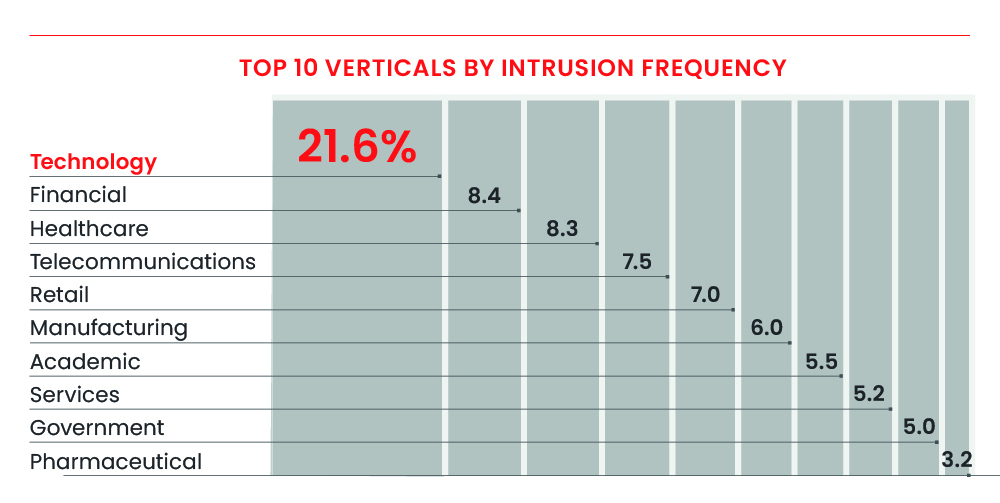
Out of all attacks, 71% were non-malware attacks, a 62% increase from the previous year. On the other hand, direct interactive attacks using keyboards, known as interactive intrusion, increased by 50% from the previous year. These sophisticated cyberattacks surpass antivirus and automated protections. The technology industry was the most frequently targeted sector. Additionally, there was a sharp increase in attacks weaponizing patched vulnerabilities, including identity-based threats and cloud vulnerability attacks.
Advertisements for access to the dark web increased by 112% from the previous year, surpassing 2,500 incidents, resulting in a 95% increase in cloud vulnerability attacks and a 200% increase in cloud threat cases compared to 2022. Interactive attack tactics, such as inducing malicious software downloads through “Vishing” and bypassing multi-factor authentication (MFA) using SIM replacement, also increased. These trends indicate a rising demand in the underground economy, making cloud environments even more attractive targets for attackers.
Establishing robust security is an essential global trend for sustaining business.
Strengthen your security system with Cloocus’s proven cloud technology and DevSecOps experts!
Related Posts

Cloocus Corp.
[United States] 500 7th Ave. Fl 8 New York, NY 10018 | Tel.+1 408.7722024 | E-mail.info_us@cloocus.com
[Malaysia] A-3A, Block A, Level 3A, Sunway PJ51A, Jalan SS9A/19, Seri Setia, 47300 Petaling Jaya. | Tel.+6016 331 5396 | E-mail.infoMY@cloocus.com
[Korea Headquarter] 6, Nonhyeon-ro 75-gil, Gangnam-gu, Seoul, Republic of Korea 06247 | Tel.02-597-3400 | E-mail.marketing@cloocus.com
[Korea Busan Campus] 55, Centum jungang-ro, Haeundae-gu, Busan, Republic of Korea | Tel.051-900-3400
[Japan] ARK Hills Front Tower, 2-23-1 Akasaka, Minato-ku, Tokyo | Tel.+81 3.5575.7808 | E-mail.infoJP@cloocus.com
Copyrights 2024 Cloocus co.,ltd. all rights reserved.




